DDoS targeted traffic comes in Plenty of unique varieties. In the case of the botnet-based mostly assault, the DDoS risk actor is employing a botnet to help coordinate the attack.
Overcommunicate with the general public. To Restrict harm to your brand’s status and make sure you hold the assault contained, only deliver required data to the general public.
Consumers who will’t use a company’s application or Site as standard typically get offended and turn to the web to trash the business.
Not very long thereafter, Georgia fell victim to Russian invasion. This attack is regarded as the textbook example of a coordinated cyberattack with Bodily warfare. It's analyzed worldwide by cybersecurity professionals and armed service groups to understand how electronic attacks can operate in tandem with Actual physical endeavours.
According to recent study DDOS assaults are don't just happening a lot more often but are Long lasting for a longer time - up from minutes to days. This then has an important effect on organization functions.
Yeshiva University has engaged Everspring, a number one company of instruction and technology providers, to support select components of method supply.
The latest DDoS attacks have also incorporated ransomware, a kind of malware attackers use to shut down the focused method right until its owners pay back a ransom.9
Infected machines range between everyday household or Place of work PCs to IoT devices — the Mirai botnet famously marshalled an army of hacked CCTV ddos web cameras — as well as their proprietors Pretty much definitely don’t know they’ve been compromised, since they proceed to function Ordinarily in most respects.
Regardless of the motivations that power these assaults, hackers can certainly be hired to help you launch a DDoS assault—out there only as guns for retain the services of. People today or entire commercial groups can be obtained for employ about the dark World-wide-web, normally under a company model, much like that of infrastructure for a assistance (IaaS) or program to be a company (SaaS).
DDoS threats may also be used in tandem with other cyberattacks. One example is, ransomware attackers may strain their victims by threatening to mount a DDoS assault Should the ransom is just not paid out.
A DDoS assault aims to overwhelm the units, providers, and community of its supposed focus on with pretend World wide web site visitors, rendering them inaccessible to or ineffective for legit customers.
The very last thing a company wishes to do is assign responsibility for DDoS response for the duration of or following an actual attack. Assign obligation prior to an attack occurs.
Protocol assaults Protocol attacks eat all accessible capacity of World wide web servers or other means, like firewalls. They expose weaknesses in Levels three and four with the OSI protocol stack to render the target inaccessible. A SYN flood is surely an example of a protocol attack, wherein the attacker sends the goal an amazing range of transmission Manage protocol (TCP) handshake requests with spoofed resource Web Protocol (IP) addresses.
Other folks require extortion, in which perpetrators attack a company and set up hostageware or ransomware on their own servers, then pressure them to pay a big money sum to the damage to be reversed.
 Danny Tamberelli Then & Now!
Danny Tamberelli Then & Now! Amanda Bynes Then & Now!
Amanda Bynes Then & Now!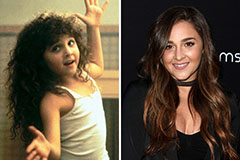 Alisan Porter Then & Now!
Alisan Porter Then & Now! Amanda Bearse Then & Now!
Amanda Bearse Then & Now!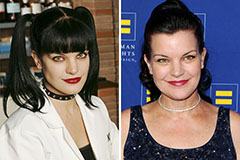 Pauley Perrette Then & Now!
Pauley Perrette Then & Now!